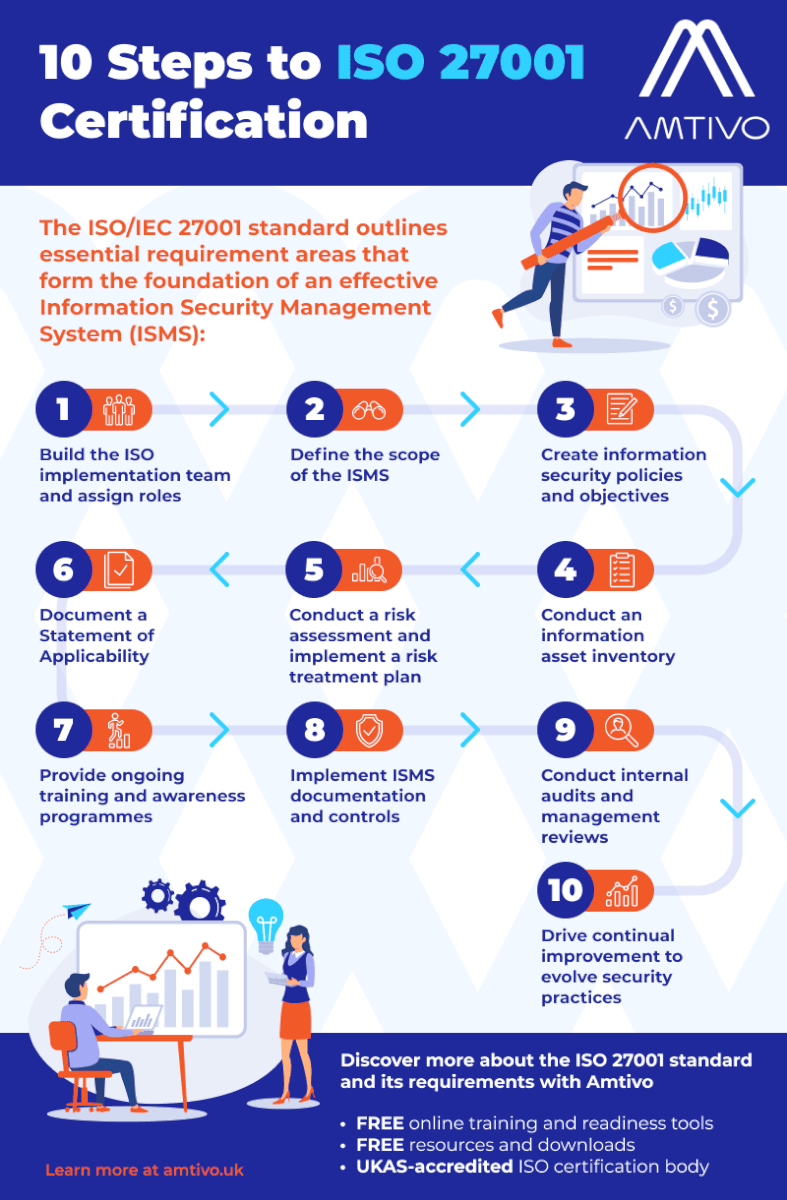
With the foundations in place, the next step is to move through the core activities that lead towards certification. The steps below outline a typical approach to keep implementation on track.
Preparation and planning
Before beginning the ISO 27001 certification process, organisation will document evidence that it has an ISMS in place that is aligned with the requirements of the standard.
An authorised project leader with specific skills and experience will typically lead the implementation. They must thoroughly understand the ISO 27001 standard and its requirements.
To begin, a preliminary review is conducted (also known as a gap analysis) of the processes and procedures in place against the ISO 27001 requirements. Once completed, findings are used to develop a clear ISMS implementation plan.
This plan involves outlining timelines, giving roles, and defining responsibilities. The plan should also list the resources required for each process. At this stage, organisations will also secure leadership support to ensure alignment and resource allocation.
The scope of the ISMS should be defined, outlining the operations the ISMS will be applied to, as well as those outside its scope.
Take our free online training course about ISO 27001 to find out more about the standard.
Establishing the ISMS
Documentation is a key part of the ISO 27001 certification process. Establishing a robust policy framework that clearly sets out an organisation’s commitment to information security. The documentation includes the ISMS scope, information security objectives, risk assessments, information security policies, and roles and responsibilities. Records of all assessments and changes are also included and can be used as evidence of compliance during audits.
An information asset inventory is conducted to identify all data and resources that need protection under the ISMS – as well as a risk assessment – which is used to implement a risk treatment plan to identify, evaluate, and prioritise potential security risks. Following this, a Statement of Applicability is documented, listing all the security controls the organisation has selected from Annex A, justifying their inclusion or exclusion.
The required ISMS documentation and controls are then implemented, ensuring all processes are clearly defined and auditable. Throughout this stage, it is important to clearly communicate everyone’s roles and responsibilities.
Training and awareness
For implementation to go smoothly and support long-term success, increasing awareness on ISO 27001 could be key. Many organisations consider providing ongoing training and awareness programmes – as regular information security training and awareness are a cornerstone of ISO 27001 compliance. To support a smooth implementation and long-term success, we provide ISO 27001 and ISMS training to help build awareness within an organisation.
Internal audit and management review
Once the ISMS has been implemented, an internal audit will allow a business to evaluate its ISMS’s effectiveness. This can be conducted by an internal team member, or consultant, who has been trained to understand the ISO/IEC 27001 standard. Discover our ISO internal auditor online training course.
Regular internal audits are crucial to assess the functioning of your ISMS. These audits will enable an organisation to identify any non-compliance or areas needing improvement – this must be done before the certification audit.
Management reviews are also necessary to assess ISMS performance and ensure alignment with organisational objectives, making adjustments as needed.
Drive continual improvement
Organisations establish a structured approach for evolving security practices as new risks emerge, so their ISMS remains effective and resilient.
Read our comprehensive guide to the ISO 27001 requirements.