From April 2024, any organisation bidding for UK local or central government contracts must meet the UK Cyber Security Standard, a mandatory baseline of risk management, network and device security, access controls, monitoring and response, and staff training, and prove compliance by holding a current Cyber Essentials certificate.
What Is the Cyber Security Standard?
Developed by the UK Government in collaboration with the National Cyber Security Centre (NCSC), the Cyber Security Standard is the latest effort to combat the risks posed by poor cyber security. It imposes certain requirements on Government departments, as well as suppliers, agencies, and contractors.
In saying this, while the Cyber Security Standard defines a baseline level of cyber security, the guidance also encourages all parties to exceed these minimum standards wherever possible. It further notes that the requirements will be strengthened over time.
Unsurprisingly, the Ministry of Defence (MOD) has its own tightly scoped requirements regarding Cyber Essentials.
In addition to Cyber Essentials, MOD contracts are governed by the Ministry of Defence’s Cyber Security Model (CSM), currently version 3, with version 4 being introduced. The CSM sets cyber security requirements based on a contract’s risk profile. Cyber Essentials is a baseline, but higher-risk contracts require additional measures.
If you’re bidding on defence contracts, have a look at our MOD Cyber Essentials Requirements Guide to help you to tick all the right boxes.
What Does the Cyber Security Standard Require?
The Cyber Security Standard is structured around similar core principles as the previous Minimum Cyber Security Standard (MCSS), such as governance, asset management, access control, vulnerability management, detection, response, and recovery.
Replacing the older framework, the Standard now requires compliance with the Cyber Assessment Framework (CAF) for critical systems – a broader, outcome-focused approach focusing on what must be achieved rather than prescribing how. It expects organisations to demonstrate how they meet each outcome. The CAF is now the required framework for government suppliers and departments.
The Standard is supported by the GovAssure process, introduced in April 2023, which requires independent assurance against CAF outcomes for critical systems.
The key requirements for businesses are as follows:
1. Comply with government security policies
Follow all relevant cross-government security policies published on GOV.UK and the Government Security pages.
2. Meet or exceed the Cyber Assessment Framework (CAF) outcomes
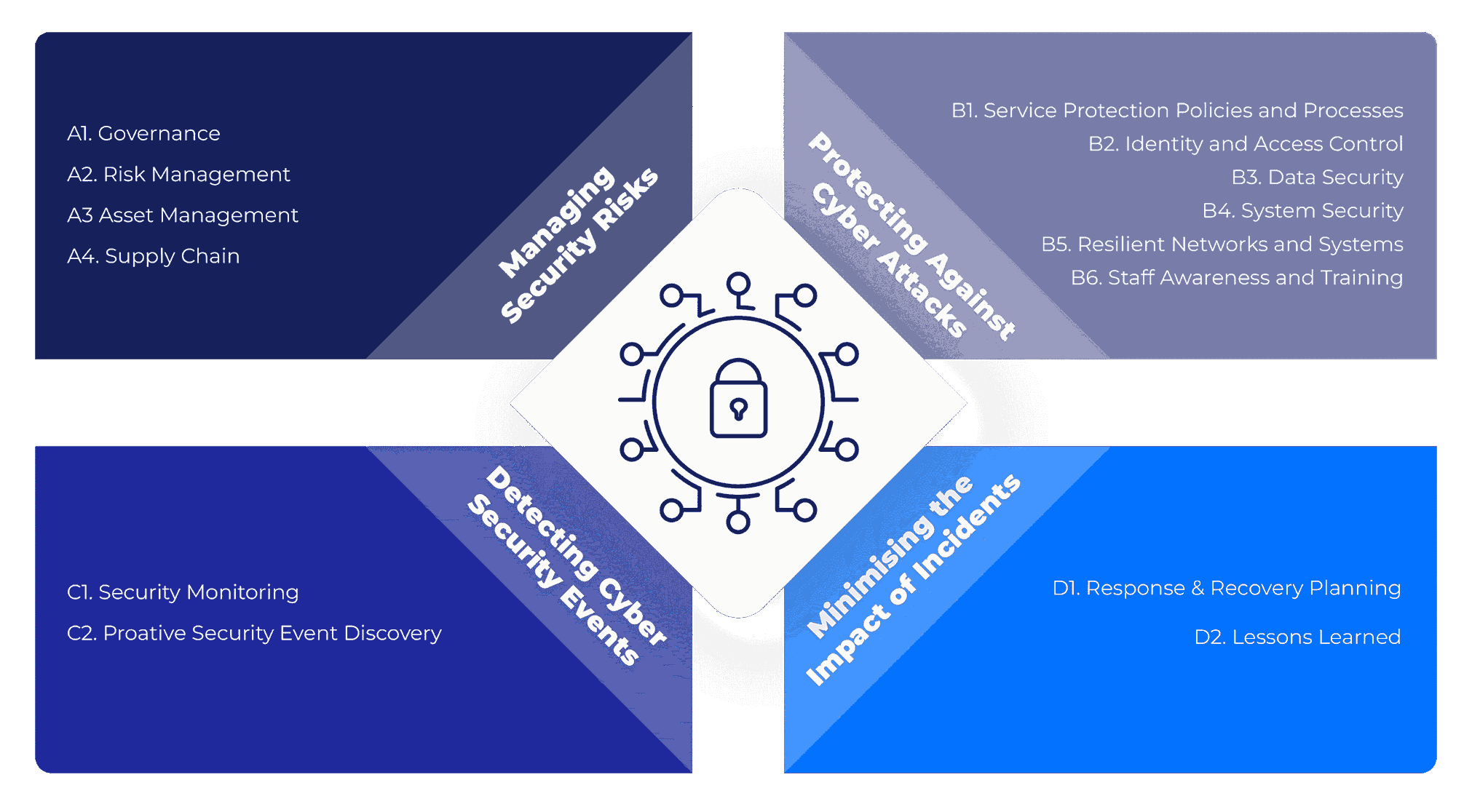
For systems critical to your contract or service, you must meet (or exceed) the security outcomes specified in the CAF, using the appropriate government CAF profile. The CAF covers four key objectives:
- Managing security risk
- Protecting against cyber attack
- Detecting cyber security events
- Minimising the impact of incidents
3. Apply CAF outcomes
While CAF is mandatory for critical systems, it is recommended that you align your broader cyber practices with CAF outcomes where feasible.
4. Undergo cyber assurance (GovAssure)
You must assure your critical systems using the GovAssure cyber assurance process, which involves independent assessment and evidence of compliance. GovAssure is mandatory for central government departments.
5. Secure by Design for new services
If you deliver new digital services or technical infrastructure, you must comply with the government’s Secure by Design principles, demonstrated via a self-assessment with a “high” confidence profile.
6. Supply chain security
You must ensure your suppliers and partners meet appropriate cyber security standards and manage third-party risks as part of your own compliance.
7. Business continuity and incident response
You need to have robust plans for responding to and recovering from cyber incidents, including regular testing and improvement of those plans.
8. Regular review and improvement
You must regularly review your cyber security arrangements and update them in response to new threats, vulnerabilities, and lessons learned from incidents.
Demonstrating Compliance in Tender Documents
In order to win any contracts from UK local or central government, suppliers will need to demonstrate that they comply with these requirements, significantly adding to the burden on suppliers to provide evidence of their suitability for a contract. As such, including a document in your tender that acts as a shorthand is the best way to demonstrate your compliance.
For instance, the Government suggests that a valid Cyber Essentials certificate could act as confirmation of compliance, meaning you could include such a certificate within your tender document.
Since February 2025, many UK government contracts require suppliers to hold a valid Cyber Essentials or Cyber Essentials Plus certificate, renewed annually. This is a formal requirement for contracts involving personal data, ICT systems, or sensitive government information. Where not held, suppliers must demonstrate equivalent controls, but this is now the exception.
Having a Cyber Essentials certificate shows that your business meets some of the security requirements set by the government. However, it’s up to the government department awarding the contract to decide – based on their own risk assessment – if this certificate is enough. In some cases, they may ask for extra evidence or higher standards, depending on the sensitivity of the contract.
The Cyber Essentials scheme was updated in April 2025 (question set v3.2) with stricter requirements on passwordless authentication, patching high-risk vulnerabilities within 14 days, and internal network segregation.
Plus, the Government is progressing with new cyber legislation. The Cyber Security and Resilience Bill, was first announced in July 2024 and further detailed in April 2025.
It is intended to expand scope to managed service providers, data centres, and improve incident reporting and enforcement.
Read more about Cyber Essentials in our cyber security guide for SMEs.
Exceeding Expectations and Winning Business
A Cyber Essentials certificate provides a solid foundation for demonstrating adherence to the Cyber Security Standard – showcasing your organisation’s commitment to essential cyber hygiene.
For many organisations, progressing from Cyber Essentials to Cyber Essentials Plus is a practical next step in strengthening cyber resilience, as it provides independent verification of your security controls.
ISO 27001 and Cyber Essentials/Cyber Essentials Plus also work well together. The former focuses on your policies and procedures for information security management, while the Cyber Essentials certifications assess the effectiveness of your technical controls and overall cyber resilience.
ISO 27001 certification is another key way to demonstrate a strong culture of cyber security throughout your organisation. It proves that your organisation doesn’t just comply with the requirements of the Cyber Security Standard, but exceeds them. A UKAS-accredited ISO 27001 certificate could also help your organisation stand out in a competitive landscape. showing that you have implemented a comprehensive, risk-based information security management system.
Read more about Cyber Essentials and how it compares with ISO 27001.
To find out more about how ISO 27001 can support your data security goals and help you win more business, take a look at our Beginner’s Guide to ISO 27001.
Enhance Your Organisation’s Cyber Security
Whether you are interested in achieving ISO 27001 certification or Cyber Essentials certification, British Assessment Bureau can help.
Get started on your journey to certification – get a quote today or contact our team of experts to discuss your needs.


